Kaspersky, a security company, has alerted regarding fresh malware aimed at cryptocurrency users via the file-sharing site SourceForge. According to their latest report, the program hosted on this platform called Office Package includes malicious code designed to target individuals involved with cryptocurrencies.
The report indicates that the Office suite of software constitutes a genuine initiative featuring Microsoft Office extensions. Nonetheless, upon deeper scrutiny, additional details emerge; notably, this collection includes download URLs that redirect to an alternate web address.
It said:
The project being investigated has been allocated the domain officepackage.sourceforge[.]io; however, the webpage shown at this address does not resemble what you would expect from officepackage on sourceforge.net.
Notably, the malware download procedure is rather intricate, requiring users to visit three different URLs prior to obtaining the file. This elaborate process seems designed to convince users that they are actually downloading a legitimate program.
Kasperksy’s cybersecurity specialists observed that the ultimate installation file is named installer.msi and has a size of 700 megabytes. Malicious parties increased its bulk to resemble a genuine software installer. Upon removing unnecessary data, the actual content turns out to be only seven megabytes.
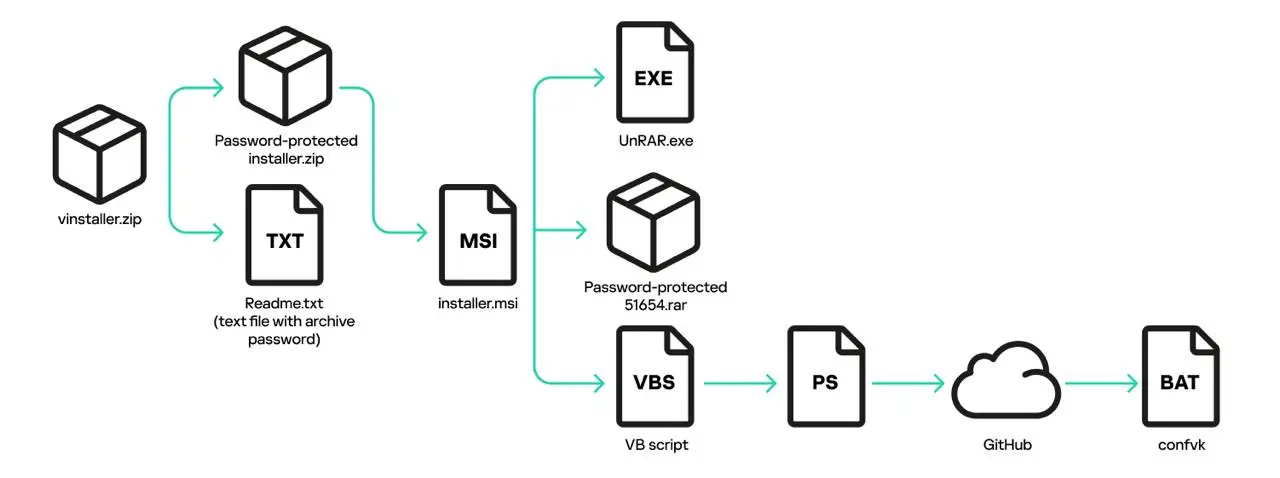
When users run the installer, they inadvertently end up installing two harmful programs on their devices: a miner and a ClipBanker. This ClipBanker application manipulates clipboard content by substituting cryptocurrency addresses copied by the user with those controlled by the hacker, causing funds to be directed to incorrect addresses.
The security experts wrote:
“The key malicious actions in this campaign boil down to running two AutoIt scripts. Icon.dll restarts the AutoIt interpreter and injects a miner into it, while Kape.dll does the same but injects ClipBanker.”
At the same time, they observed that the assault was primarily aimed at Russian targets. Evidence of this includes the use of a Russian-language interface on the officepackage.sourceforge[.]io website and the statistic that out of 4,604 affected users from January through late March, 90% were based in Russia.
Address poisoning scams increasing
The Kaspersky report aligns with the surge in address poisoning attacks targeting cryptocurrency users, which has been noted by various blockchain security companies. Data from Scam Sniffer indicates that one of the largest phishing incidents in March resulted from address poisoning, ranking as the third biggest such event during that month.
Cyvers also noted that address poisoning scams resulted in losses exceeding $1.2 million during the initial three weeks of March, building upon the $1.8 million lost in February. According to the company, their AI-driven threat detection system uncovered a rise in such attack instances.
Although many cases of address poisoning attacks stem from hackers manually transmitting minor transactions to targets using addresses closely resembling those they commonly interact with, the deployment of advanced malware enabling attackers to alter addresses found in clipboards demonstrates how malicious parties keep adapting their strategies.
According to security professionals, the primary remedy for this issue is for users to refrain from downloading software from unreliable sites. These experts pointed out that malicious entities often use unauthorized software platforms to spread harmful programs, so individuals who frequent these sites should stay vigilant about potential risks.
Nevertheless, they pointed out that this malware poses an even greater issue since it offers a novel method for hackers to infiltrate compromised systems. Consequently, there is a risk that the developers might choose to utilize it beyond just targeting cryptocurrency users and instead opt to sell it to even more malevolent adversaries.
MaximusAcademy: Interested in expanding your wealth in 2025? Discover how to achieve this through DeFi in our forthcoming online class. Save Your Spot
